CrowdStrike Holdings, Inc. Strategy Analysis

Editor-reviewed by Ahmad Zaidi based on analysis by TransforML's proprietary AI
CEO, TransforML Platforms Inc. | Former Partner, McKinsey & Company
Strategy overview for CrowdStrike Holdings, Inc.
CrowdStrike's strategy is centered on expanding its AI-native, cloud-delivered Falcon platform to consolidate cybersecurity across endpoints, cloud workloads, identity, data, and IT operations. The company is focused on driving customer growth by replacing legacy security tools, increasing module adoption within its installed base, and expanding internationally, while deepening differentiation through AI-driven threat detection, agentic AI capabilities, and managed security services. Following recent operational challenges, CrowdStrike is also prioritizing software resiliency, platform reliability, and trust restoration, alongside continued investment in research and development, ecosystem partnerships, and platform extensibility to strengthen its leadership position in next-generation cybersecurity
Key Competitors for CrowdStrike Holdings, Inc.
Palo Alto Networks
Major cybersecurity platform competitor with broad portfolio of security products, strong enterprise presence, and significant R&D investment in AI and automation.
Symantec (Broadcom)
Legacy antivirus leader with established customer base, broad product range, and strong brand recognition in enterprise security.
McAfee
Traditional endpoint security provider with large installed base, consumer and enterprise offerings, and strong channel partnerships.
SentinelOne
Direct endpoint security competitor with AI-powered platform, cloud-native architecture, and strong growth in enterprise market.
Microsoft Defender
Built-in Windows security solution with deep OS integration, broad deployment, and competitive pricing for Microsoft ecosystem customers.
Trend Micro
Enterprise security vendor with comprehensive threat protection, strong presence in Asia-Pacific, and hybrid cloud security solutions.
Sophos
Endpoint and network security provider with unified security platform, strong channel focus, and comprehensive threat intelligence.
Insights from CrowdStrike Holdings, Inc.'s strategy and competitive advantages
What Stands Out in CrowdStrike Holdings, Inc. strategy
CrowdStrike's strategy is uniquely distinguished by its cloud-native purity and its deeply integrated human expertise. Unlike competitors like Palo Alto Networks, which is consolidating a broad portfolio of often-acquired technologies, CrowdStrike's Falcon platform was built from the ground up as a cloud-first, single-agent architecture. This provides a distinct advantage in deployment speed, scalability, and ease of use, directly supporting its 'Rapid Time to Value' strength.
For example, where Palo Alto focuses on integrating disparate products via its 'Platformization' strategy, CrowdStrike's core is already a unified system. Furthermore, CrowdStrike's emphasis on services like 'Falcon Complete Next-Gen MDR' and 'Counter Adversary Operations' embeds elite human intelligence directly into its offering. This contrasts with Palantir's approach of providing a tool (AIP, Foundry) for an organization's own people to use; CrowdStrike sells a managed outcome—'to stop breaches'—which is a powerful differentiator for customers lacking deep in-house security expertise.
What are the challenges facing CrowdStrike Holdings, Inc. to achieve their strategy
CrowdStrike faces significant challenges from the intense 'platformization' competition and the escalating AI narrative arms race. Its primary competitor, Palo Alto Networks, is aggressively pursuing the same consolidation message but with a larger existing customer base and a broader portfolio that includes network hardware. Palo Alto's ability to bundle and discount across its vast offerings (with a Remaining Performance Obligation of $12.7 billion) creates substantial pressure on CrowdStrike's customer acquisition and expansion strategy.
A second major challenge is the AI arms race. While CrowdStrike touts its 'AI-native Falcon platform', competitors are making similar claims; Palo Alto heavily markets its 'Precision AI™' and Palantir has its 'Artificial Intelligence Platform (AIP)'. CrowdStrike must continually prove that its AI, powered by the 'Security Cloud', delivers tangibly superior outcomes to cut through the marketing noise. Finally, the strategic initiative to 'Enhance Software Resiliency' following a major incident highlights a potential vulnerability in customer trust, an area that deeply entrenched competitors will undoubtedly seek to exploit.
What Positions CrowdStrike Holdings, Inc. to win
Cloud-Native Architecture
- CrowdStrike's Falcon platform is built entirely in the cloud, enabling the collection and analysis of a massive, crowdsourced dataset to stop breaches. The platform is designed to be redundant, resilient, and high-performing, delivering security with agility and ease of use.
AI-Powered Security
- CrowdStrike leverages Al to transform cybersecurity, combining Al for cybersecurity with cybersecurity for Al. The Falcon platform's Al-native architecture uses advanced models and the power of the Security Cloud to detect and stop breaches.
Single Agent Platform
- CrowdStrike uses a single, lightweight agent that is installed on each endpoint or cloud workload. This agent incorporates identification and prevention of known and unknown malware and fileless attacks using machine learning, Al, exploit blocking, and advanced behavioral techniques.
Threat Graph Technology
- CrowdStrike's Threat Graph is a proprietary, powerful, scalable, and dynamic graph database that continually looks for malicious activity by combining Al with behavioral pattern-matching techniques to track the behaviors of every OS process and software program executed on an endpoint.
Counter Adversary Operations
- CrowdStrike's Counter Adversary Operations include proactive threat hunting and intelligence capabilities. These solutions leverage the insights of elite security experts and the power of Threat Graph to identify and mitigate advanced threats, providing customers with actionable intelligence to strengthen their defenses.
Managed Services Subscription
- Falcon Complete Next-Gen Managed Detection and Response (MDR) delivers a comprehensive managed security service subscription that combines 24/7 expert monitoring, investigation, response, and remediation to stop breaches across the entire attack lifecycle.
Platform Consolidation
- The cloud-native platform gives customers a unified approach to address their most critical areas of risk seamlessly. CrowdStrike empowers customers to rapidly deploy and scale industry leading technologies across multiple areas from a single platform.
Rapid Time to Value
- The cloud-native platform was built to rapidly scale industry leading protection across the entire enterprise, eliminating lengthy implementation periods and professional services engagements that next-gen and legacy competitors may require.
What's the winning aspiration for CrowdStrike Holdings, Inc. strategy
CrowdStrike aims to transform the cybersecurity industry by establishing its Security Cloud as the leading platform for breach prevention. It seeks to empower organizations with a unified, AI-driven approach that simplifies security operations, reduces costs, and provides superior protection against increasingly sophisticated threats.
Company Vision Statement:
Company Vision Statement - To be the definitive platform for cybersecurity consolidation, purpose-built to stop breaches.
Where CrowdStrike Holdings, Inc. Plays Strategically
CrowdStrike competes in the cybersecurity market, focusing on endpoint and cloud workload security, managed security services, and adjacent areas like identity protection and IT operations management. The company targets organizations of all sizes across various industries, expanding its international footprint while also focusing on the U.S. public sector.
Key Strategic Areas:
How CrowdStrike Holdings, Inc. tries to Win Strategically
CrowdStrike wins by leveraging its cloud-native architecture, AI-driven innovation, and single agent platform to deliver superior threat detection and prevention. The company's value proposition includes ease of adoption, rapid time-to-value, and reduced total cost of ownership, enabling customers to transform their security operations from reactionary to predictive.
Key Competitive Advantages:
Strategy Cascade for CrowdStrike Holdings, Inc.
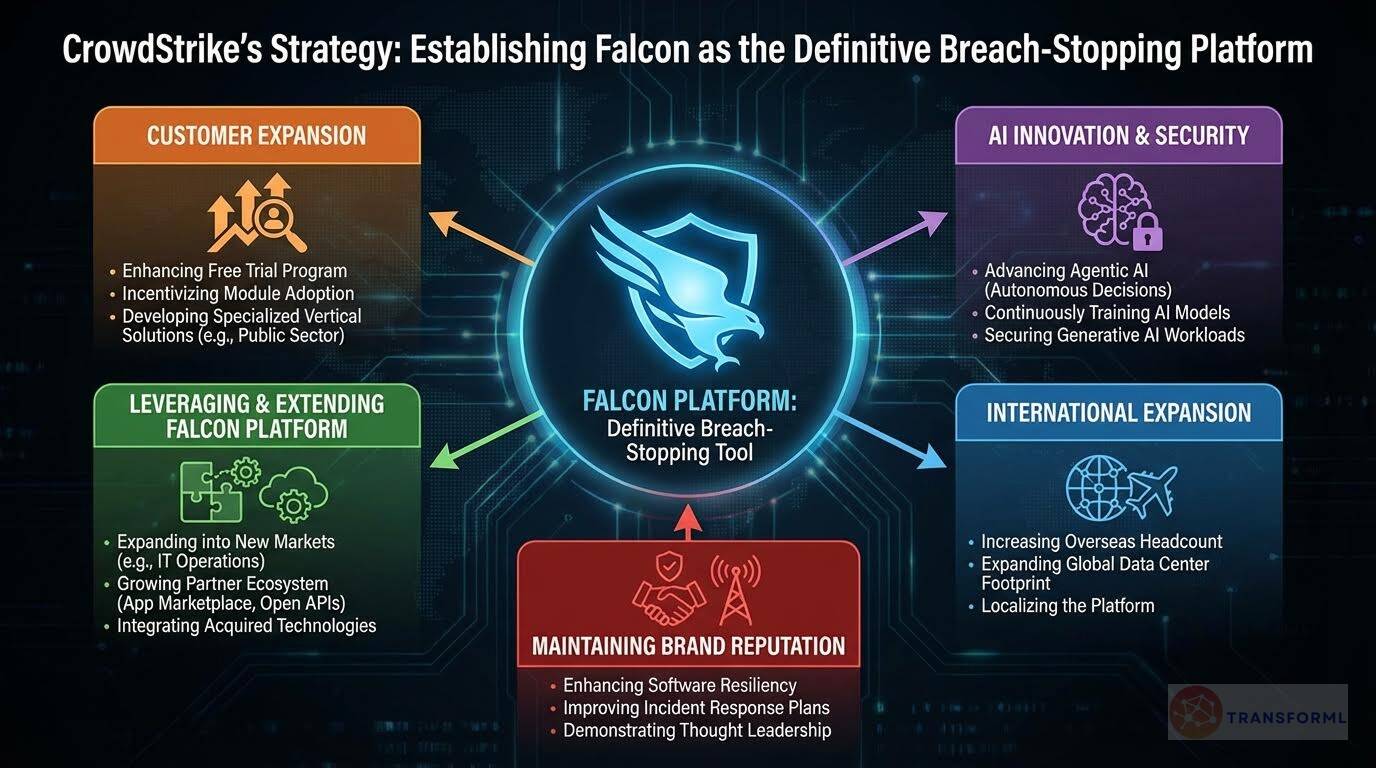
Below is a strategy cascade for CrowdStrike Holdings, Inc.'s strategy that has been formed through an outside-in analysis of publicly available data. Scroll down below the graphic to click on the arrows to expand each strategic pillar and see more details:
Related industry articles:
Expand Customer Base
Grow the customer base by replacing legacy endpoint security products and penetrating existing customers with additional cloud modules and endpoint deployments.
Enhance Free Trial Program
Improve the free trial program of Falcon Prevent to drive customer acquisition by making it easier to download from the website and AWS Marketplace.
Incentivize Module Adoption
Offer in-application trial usage of additional modules to cross-sell to existing customers and drive adoption of more cloud modules.
Develop Verticalized Solutions
Create tailored solutions for specific verticals, such as the U.S. public sector, to broaden reach into new customer segments.
Improve Customer Success Program
Improve customer success programs to ensure customers fully utilize their product subscriptions, leading to higher renewal rates.
Drive Al Innovation and Security
Pioneer in leveraging Al to transform cybersecurity, combining Al for cybersecurity with cybersecurity for Al.
Advance Agentic Al Capabilities
Develop and deploy agentic Al capabilities, such as Charlotte Al, to deliver autonomous security decisions within customer-defined guardrails.
Enhance Al Model Training
Continuously train Al models with high-fidelity data from the Security Cloud to improve threat detection and prevention.
Secure Generative Al Workloads
Develop solutions to help customers safeguard generative Al applications, protect sensitive data, and mitigate the risks posed by Al misconfigurations and vulnerabilities.
Integrate Al into Existing Modules
Incorporate Al-powered features into existing Falcon platform modules to enhance their functionality and effectiveness.
Leverage Falcon Platform
Enter new markets and broaden reach into new customer segments by leveraging the Falcon platform's single data model and open cloud architecture.
Develop IT Operations Use Cases
Expand Falcon Discover to include use cases outside of security, such as application license management, AWS spend analysis, and asset inventory.
Enhance Falcon Complete Offering
Enhance Falcon Complete to create a solution for customers with limited or no internal security expertise.
Expand Government Compliance
Obtain and maintain government certifications, such as FedRAMP, to broaden reach into U.S. public sector verticals.
Integrate Acquired Technologies
Rapidly integrate recently acquired technologies into the Falcon platform to provide customers with a unified set of cloud-delivered technologies.
Expand Internationally
Grow the international customer base by increasing investments in overseas operations, including adding headcount and expanding data centers.
Increase Overseas Headcount
Add headcount in Europe, the Middle East, Asia-Pacific, including Japan, to grow the international customer base.
Expand Data Center Footprint
Expand data centers overseas to support international operations and customer growth.
Localize Falcon Platform
Localize the Falcon platform for international markets, including translation into foreign languages and adaptation for local practices and regulatory requirements.
Establish International Partnerships
Develop and strengthen relationships with channel partners in international markets to expand reach and sales.
Extend Falcon Platform and Ecosystem
Design the architecture to be open, interoperable, and highly extensible, empowering partners and customers to build their own capabilities on top of the Falcon platform.
Expand Open APIs
Expand the set of open APIs to allow customers and partners to build their own capabilities on top of the Falcon platform.
Develop Falcon Foundry Platform
Further develop the Falcon Foundry no-code application development platform to allow customers to quickly create their own apps.
Grow CrowdStrike Marketplace
Continue investing in the CrowdStrike Store to empower partners by making it easier to build applications and to enable customers to more easily discover, try, and purchase additional cloud modules.
Integrate Partner Solutions
Actively seek out and integrate with complementary security solutions to enhance the Falcon platform's capabilities and provide a more comprehensive security ecosystem.
Maintain Brand Reputation
Maintain and enhance the CrowdStrike and Falcon brands and reputation as a provider of high-efficacy security solutions.
Enhance Software Resiliency
Invest in enhancements to software resiliency, testing, and customer controls to prevent future incidents like the July 19 Incident.
Improve Incident Response Plan
Enhance the incident response plan and process for detecting, mitigating, and investigating security incidents.
Engage in Thought Leadership
Deliver targeted content to demonstrate thought leadership in the security industry, including speaking engagements, regular reports, and educating the public about cybersecurity threats.
Manage Media Relations
Proactively manage media relations to address negative publicity and maintain a positive brand image.
Read more about industry strategies
Source and Disclaimer: This analysis is based on analysis of Annual reports for 2025. For informational purposes only (not investment, legal, or professional advice). Provided 'as is' without warranties. Trademarks and company names belong to their respective owners.